In yesterday’s Patch Tuesday, Microsoft released 128 new patches. Critical patches targeting protocols such as RPC, SMB, NFS, LDAP, Hyber-V, and should be patched immediately due to the fact that they are Remote Code Execution bugs. RPC vulnerability [CVE-2022-26809] could spawn a worm similar to Blaster [MS03-026], which Microsoft believes to have infected anywhere around 8-18 million computers totaling approximately $320m of damage. In 2017, we had WannaCry/NotPetya after a critical SMB vulnerability disclosure. The attack was estimated to have affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars. It is important to note that as of this blog post, there hasn’t been any known and publicly disclosed POCs for the below critical vulnerabilities.
🚩CRITICAL
[.] RPC
CVE-2022-26809 – CVSS 9.8
[.] SMB
CVE-2022-24541 – CVSS 8.8
CVE-2022-24500 – CVSS 8.8
[.] NFS
CVE-2022-24491 – CVSS 9.8
CVE-2022-24497 – CVSS 9.8
[.] LDAP
CVE-2022-26919 – CVSS 8.1
[.] Hyber-V
CVE-2022-23257 – CVSS 8.6
CVE-2022-24537 – CVSS 7.7
CVE-2022-22008 – CVSS 7.7
⚠️IMPORTANT
Below patches aren’t labeled as critical, however since they could be paired up with above RCEs they should be also patched as soon as possible. We would like to point out that these vulnerabilities have been reports to Microsoft by National Security Agency (NSA), and CrowdStrike.
CVE-2022-24521 – Windows Common Log File System Driver Elevation of Privilege Vulnerability – CVSS 7.8
CVE-2022-26904 – Windows User Profile Service Elevation of Privilege Vulnerability – CVSS 7
- Public Metasploit exploit available
ℹ️ Shodan shows a large number of hosts with ports 445 open to the world, and we can’t stress enough that these ports should never be exposed to the world. Audit your firewalls to avoid being part of an automated attack!
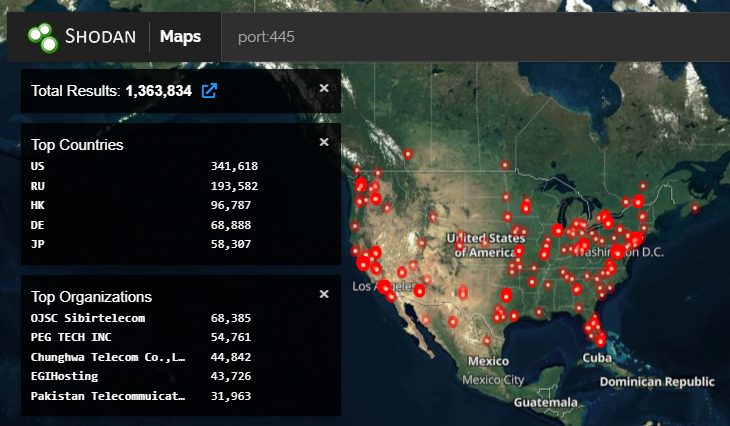
[.] Recommendations
- Apply patches ASAP
- Audit firewall rules
- Filter network traffic: TCP and UDP ports 135, 139 and 445
- SIEM alerts for malicious activity monitoring